1. Install AWS CLI
- Download the macOS pkg file: http://awscli.amazonaws.com/AWSCLIV2.pkg
- Double-click the downloaded file to start the installer.
- Follow the on-screen instructions to install the AWS CLI.
2. Create an AWS user for AWS CLI operations
This procedure is performed using the AWS Management Console.
1) On the IAM screen of the AWS Management Console, select "Users" and click "Create users."

2) Enter any name in "User name" and click "Next"



5) The screen will transition to a list of IAM users, so open the IAM user you created.


7) Scroll down and click "Create access key" under Access keys.

8) Select Application running outside AWS and click Next


10) If you see "Access key created", the process is successful. Please keep a copy of the Access key and Secret access key in a secure environment as you will need them in the next step.

Once you close this screen, you will not be able to view your secret access key again, so please be sure to write it down.
3. Configuring the AWS CLI
1) Create a configuration file for AWS CLI authentication Execute the following command in the terminal. (This will create a configuration file for AWS CLI authentication.)
$ aws configure- AWS Access Key ID:Enter the number you wrote down during the step “2. Create AWS users to perform AWS CLI operations.”- AWS Secret Access Key:Enter the number you wrote down during the step “2. Create AWS users to perform AWS CLI operations.”- Default region name: You can enter any region, but unless otherwise specified, set the region to “ap-northeast-1.” ※- Default output format: You can leave this field empty.
Please make sure that the region setting matches the AWS KMS management console! You can check this in the pull-down menu in the top right of the management console.
2) Applying the AWS CLI authentication file Execute the following command in the terminal. (When you execute it, the authentication file created in ① above will be reflected in the AWS CLI.)
$ export AWS_REGION=YOUR_REGION
$ export AWS_PROFILE=YOUR_PROFILE4. Download and configure nsuite-kmscli
1) Access the nsuite-kmscli Github repository https://github.com/doublejumptokyo/nsuite-kmscli

3) Click "nsuite-kmscli-macOS.zip" to download the executable file.
Extract the downloaded “nsuite-kmscli-macOS.zip” folder and save the “nsuite-kmscli” file to a directory of your choice.

4) Grant file access permissions. On your terminal, navigate to the directory where the “nsuite-kmscli” file is located and execute the following command.
$ chmod 777 nsuite-kmscli5. Creating a private key
1) Execute the command to create a private key In the terminal, while in the directory that contains "nsuite-kmscli", execute the following command (if the command is executed successfully, a private key will be created in AWS KMS.)
$ ./nsuite-kmscli new
2) If you run the command and the following pop-up appears, click "Cancel", perform the "File authentication procedure", and then run the command again.
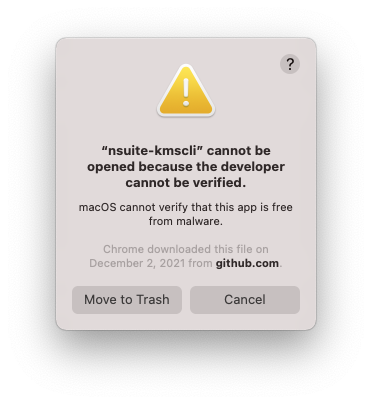
File authentication procedure:
1) Right-click in Finder and click "Open" from the menu that appears.
5. Creating a private key
1) Execute the command to create a private key In the terminal, while in the directory that contains "nsuite-kmscli", execute the following command (if the command is executed successfully, a private key will be created in AWS KMS.)
$ ./nsuite-kmscli new2) If you run the command and the following pop-up appears, click "Cancel", perform the "File authentication procedure", and then run the command again.

1) Right-click in Finder and click "Open" from the menu that appears.


3) Check the private key you created If you run the command below, the addresses corresponding to the private key you created in AWS KMS will be displayed in a list, and you can confirm that the private key has been created. (The private key itself will not be displayed.)
$ ./nsuite-kmscli listWas this article helpful?
That’s Great!
Thank you for your feedback
Sorry! We couldn't be helpful
Thank you for your feedback
Feedback sent
We appreciate your effort and will try to fix the article